InfraSec 2: Balancing cyber resilience against other priorities in AMP7 and beyond
The water sector often has the luxury of relying on the fact it is a less visible target for cyber attacks than other critical national infrastructure (CNI). The sector has not faced a high profile cyber attack in recent years, and as one CISO put it to us “after all, water doesn’t blow up”. But those with responsibility for building resilience in our drinking water supply are facing new threats and changing regulation from its 15 different regulatory bodies. High (if slightly vague) expectations on resilience and innovation were set within Price Review 2019 (PR19), with individual Asset Management Plans for 2020-2025 (AMP7) reflecting the increasing importance of cybersecurity at a board level.
CyberOwl has been spending time with those responsible for cybersecurity within the water market and the government bodies responsible for translating legislation into practical guidance. This is an investment we make regularly as an important part of continuously developing our ability to service the sector, our product and technology roadmap. In March, in partnership with the London Office for Rapid Cybersecurity Advancement (LORCA), we hosted InfraSec 2, the second event in a growing series aimed at gathering cybersecurity leaders and practitioners from top UK water organisations.
PR19, AMP7 and cyber security
PR19 was implemented with a key theme at its heart: to push water companies to go further than ever before; improving efficiency, customer service and, most interestingly, resilience. Initial assessment of the UK water companies’ AMP7 submissions by Ofwat resulted in no company’s business plan being awarded ‘exceptional status’ for being sufficiently ambitious, innovative and high quality. Just 3 of 17 UK water companies were given the green light to begin delivering their plans. The remaining companies had their plans either slow-tracked or marked down as requiring significant scrutiny. Some of the AMP 7 plans were specifically criticised for the lack of a robust strategy to build cyber resilience. The companies that did not have their AMP7 fast-tracked have been busy defending, improving and resubmitting their plans, which were due in April.
As the resubmitted plans are being considered by Ofwat, we thought this was a meaningful time to gather CISOs across the water companies to reflect on the feedback from Ofwat relating to the cyber resilience plans, how this translated into practical challenges the CISOs were facing on the ground and some calls to action.
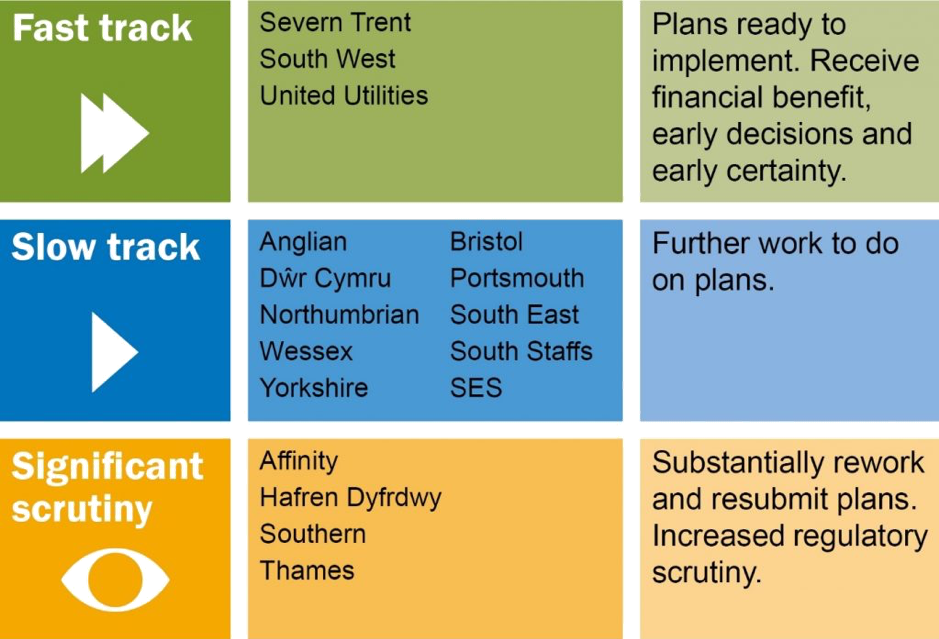
Ofwat initial assessments of AMP7 Plans
Securing Operational Technology (OT) is planned in for the first time…
This is the first AMP where specific budgets were submitted to invest in the protection of SCADA, industrial control systems (ICS) and industrial IoT (IIoT). Given escalating threats targeting OT, this is clearly a positive development for the sector. The main driver appears to be the NIS Directive. Consequently, the majority of organisations appear to have focused investments during the period in building capability within treatment and distribution of drinking water; the critical services where NIS Directive has reach. Wastewater treatment on the whole, has been given lower priority. This is despite a steady increase in turning wastewater sludge into renewable energy and ambition to connect this to the grid, presenting rather different cyber-physical and safety risks to wastewater treatment processes.
…but cost constraints drive the need to prioritise
Affordability is a key area in PR19. A number of the business plans received feedback from Ofwat demanding significant efficiency gains. This has translated into plans that feature cost savings sitting high on the agenda. There are early signs that investment in OT security may be hampered by the cost constraints of PR19. In a number of cases, the feedback on the lack of affordability in the AMP 7 plans have cascaded down into slashing over 50% of the OT security budget in the resubmitted plans. Boards will need to understand that this simply means they will need to live with a higher level of cyber risk to their OT estate. For CISOs, this forces them to make some hard choices on where to spend a smaller amount of investment. They will need to get a clear understanding of the key water treatment and distribution processes in order to get a good handle on which controls to prioritise in order to maintain critical services. This will require a closer working relationship between the CISO and the Operations / Asset Manager.
Collaboration is needed beyond the CISO network
The water sector benefits from not being competitive and already actively collaborates on threat intelligence through informal, but currently adequate channels. This proved highly useful during the Wannacry attack. There is great need to strengthen this collaboration beyond just the CISO network. Boards would benefit from a forum to inform and educate one another in their journeys towards being both compliant and resilient. To the extent this is not already happening, Competent Authorities would benefit from active dialogue and comparing their separate approaches to regulating for the NIS Directive.
Our mission at CyberOwl is to develop and deliver technologies that enable a risk-based cyber-physical defence posture. This aligns with the resilience objectives of PR19 and feedback on AMP7 submissions. It is clear there needs to be more clarity on where to invest spending on security, particularly across the OT estate. Better decisions need to be made.
We have launched a study to develop an in-depth view of the key cyber risks across the drinking water treatment and distribution processes. The objective is to develop a framework for prioritising where to invest in greater visibility across the OT estate. We would certainly welcome inputs on this. Please get in touch if you would like to be involved, or to find out more about what we do, by email: info@cyberowl.io or call us at +44 (0) 208 050 8042


